Create A New Networkpolicy Named Allow from ns port In The Existing Namespace
The text explains the concept of NetworkPolicy in Kubernetes and how it can be used to restrict traffic between pods in a namespace. It discusses the various parameters, such as rules, ports, and namespaces, that can be defined in a policy. The article also mentions that without any policies set, Kubernetes allows all communications between pods. An example of defining a policy for allowing traffic from specific pods with certain labels on a specific port is also given.
To create a new NetworkPolicy named allow-from-ns-port in the existing namespace dev1, you can use the following YAML manifest:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-from-ns-port
namespace: dev1
spec:
podSelector:
matchLabels:
purpose: production
ingress:
- from:
- namespaceSelector:
matchLabels:
name: dev2
ports:
- port: 9000
protocol: TCP
This NetworkPolicy allows Pods in namespace dev2 to connect to port 9000 of Pods in namespace dev1. It meets the requirements by ensuring that it does not allow access to Pods which don't listen on port 9000 and does not allow access from Pods which are not in namespace dev2 with the label "purpose=production".
You can apply this NetworkPolicy using the kubectl apply -f <filename>.yaml command, where <filename>.yaml is the name of the file containing the YAML manifest.
If you have further inquiries or need additional assistance, feel free to ask!
Sources
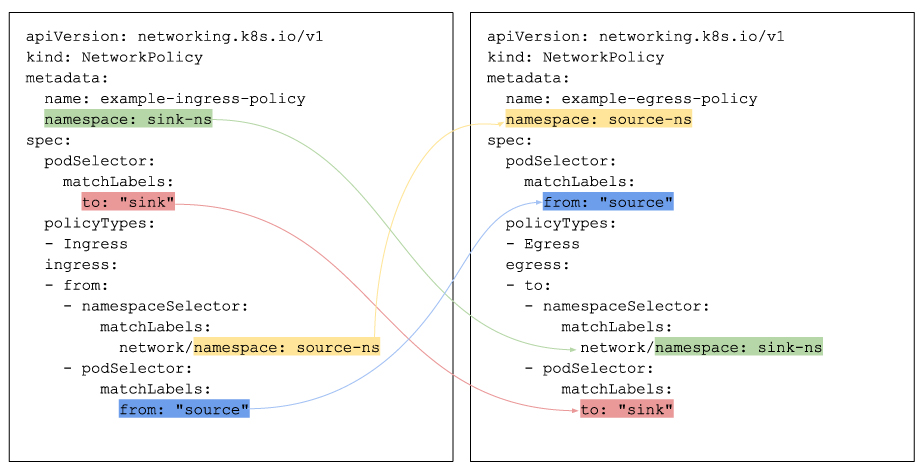
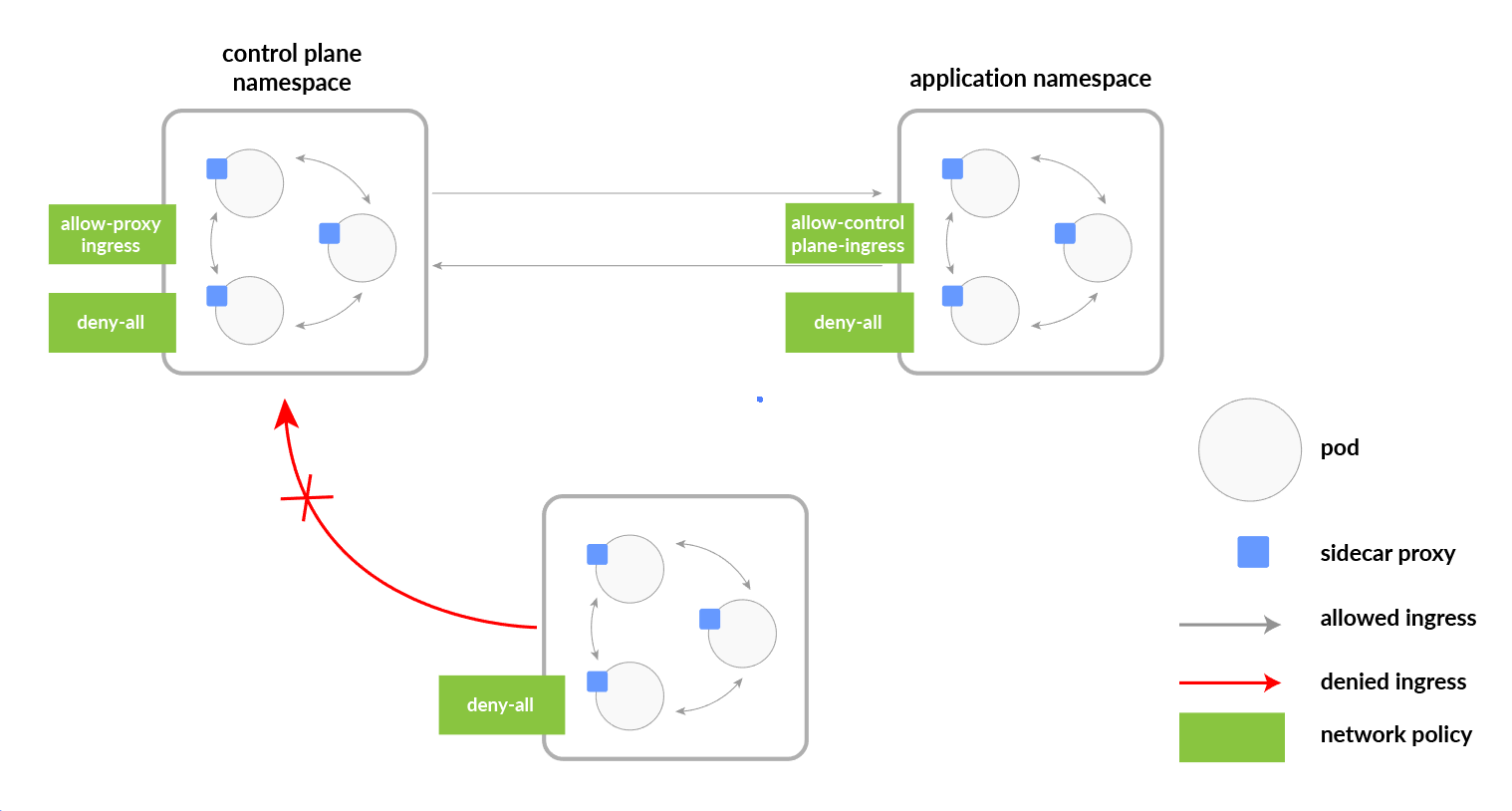
Related Questions
Work fast from anywhere
Stay up to date and move work forward with BrutusAI on macOS/iOS/web & android. Download the app today.
